- Products & Services
CeOne-CONNECT Private Network
-
MPLS (Premium)
Fully Meshed Managed Private Network with Guaranteed QoS
SD-WAN (Hybrid)
Redefine your Business Agility and Advantages
Multi-Cloud Connect
Embrace More Possibilities to Achieve Greater Business Value
Ethernet (VPLS)
Efficient Private LAN Connectivity
MPLS Provision with IPSec Encryption (Express)
Speedy Provision Private Network with IPSec Encryption
Secure Access Service Edge (SASE)
Redefine your Business Agility and Advantages
Remote Access to MPLS (Remote)
Secure Remote Access to MPLS Private Network
Managed WAN Optimization (Accelerator)
Managed WAN Optimization Services Accelerating SPEED - Enabling BIZ
Information Security
-
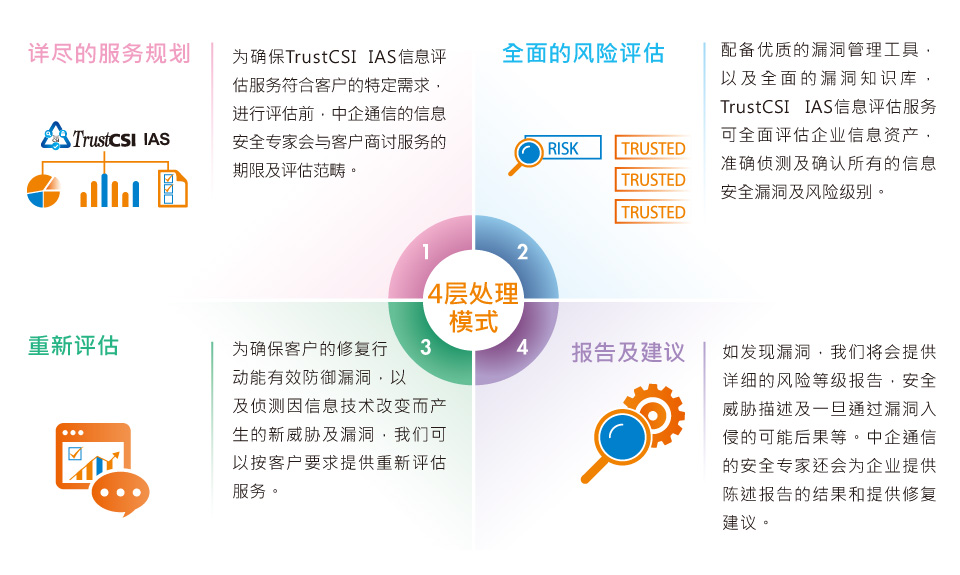
Identify & Predict
Assessment Services
Asset Identification ServiceVulnerability Assessment ServicePenetration Test ServiceCode Review ServiceAI Visual SecurityProtect
Managed Network Security Device Service
Managed Next-Generation Firewall (NGFW)Unified Threat Management (UTM)Managed Web Application Firewall (WAF)Network SecuritySecure Access Service Edge (SASE)Mail SecurityMail Protecition ServiceDetect
Threat Detection Services
Endpoint Detection & Response (EDR)Managed Security Services (MSS)Traffic Monitor and AnalysisTrustCSI Secure AINetwork Traffic AnalysisRespond & Recover
Security Response Services
Security Orchestration, Automation and Response (SOAR)Threat Hunting ServiceSecurity Incident Response (IR)Backup & Disaster Recovery as a ServiceVirtualized Backup, Replication & Recovery (BRR)
SmartCLOUD Cloud Solutions
-
IaaS – Infrastructure as a Service
Cloud Computing (Compute) Dedicated Private Cloud (vONE)
PaaS - Platform as a Service
SaaS – Software as a Service
Cloud Email & Collaboration Suite (M@il)
XaaS – Anything as a Service
Backup & Disaster Recovery as a Service Virtualized Backup, Replication & Recovery (BRR) Storage as a Service Object Storage Solution (OS) Virtual Desktop as a Service Managed VDI (DaaS Lite)
Managed Service
Cloud Connectivity
- Solutions
Solutions
MoreSolutions
- Technology & Services
Technology & Services
MoreTechnology & Services
- About Us
- Resources Center
Resources Center
MoreResources Center
- Contact Us
Contact Us
MoreContact Us